“In preparing for battle I have always found that plans are useless, but planning is indispensable.”
– Dwight D. Eisenhower
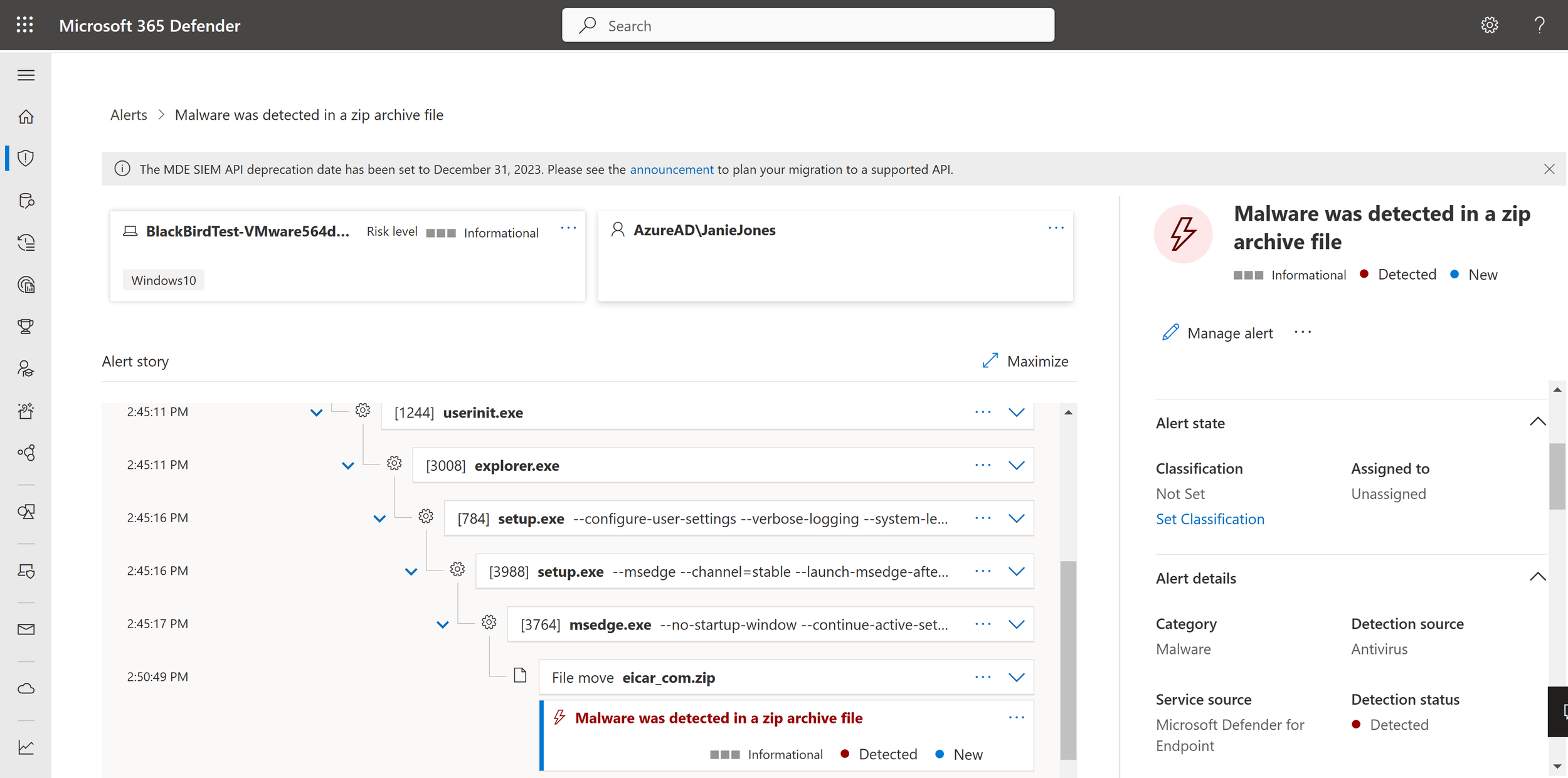
Real-Time Detection and Response
Simply put, basic anti-virus coverage is no longer enough, especially if you are working with customer data. It is easily evaded and constantly outdated. Get access to the same endpoint protection used by fortune 500 companies that provides real-time protection and alerting.
Email Security
Phishing emails remain one of the most common initial attack vectors for malicious actors, because they work.
Protect your staff from phishing emails, malicious attachments, send out test phishing campaigns, and provide employees with proper training.
Vulnerability Assessments
Everyone is looking for a handout, and attackers will always target low hanging fruit first. Locating and remediating the weak points in your IT infrastructure is the first step in strengthening your posture.